Overview
n2record is a comprehensive, secure, easy-to-use web-based solution that streamlines and standardizes your entire workflow for recorded statements. Using any phone, digital recorder or, n2record mobile, our iPhone app, you can capture, store, share, and transcribe statements from one unified platform. Adjusters consistently rate our products outstanding and easy to use.
Benefits your entire claims organization
n2record streamlines the recorded statements process, replacing ad-hoc, time consuming, and expensive processes with digital files that can be easily accessed and shared throughout your claims organization.
Supports best practices
- Replaces multi-step manual processes with one digital process
- Lets you instantly share data within your claims organization and with approved outside parties
- Delivers more consistent and accurate recorded statements so you can make better decisions
- Reduces Expenses
Gives managers real-time visibility
- Provides insight into the interview process by line of business or individual
- Ensures claims representative compliance
- Identifies training needs with real-time reporting
Reduces expenses
- No new IT investment or integration needed to realize immediate benefits
- Saves the time and expense of building and maintaining an in-house solution
- Eliminates storing, shipping, and handling cassette tapes
What does it cost?
With n2record you get lifetime storage of your statement data with no hidden fees. Pricing varies by volume, so ask for a custom quote today.
How It Works
n2uitive’s web-based n2record requires no hardware, software, or IT integration—and you will be up and running in a matter of days. Here’s how it works:
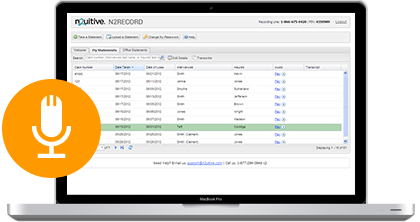
Record
Just dial our toll-free number, conference in your participants, enter your claim number, and start recording the interview. When participants hang up, your conversation will be digitized, encrypted and posted to your personal statement library. Interviews recorded using a handheld digital recorder can be easily uploaded directly using any web-browser.

Listen
Once interviews are completed, the digital audio files are securely stored in n2uitive’s database to meet insurer specific retention periods. They are available to review with a simple click of the button.
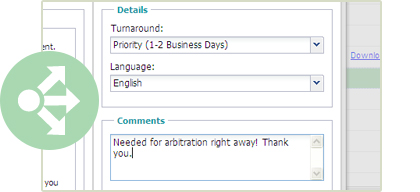
Share or transcribe
With a single click you can easily and securely share or send files from your statement library to approved outside parties or your transcription provider.
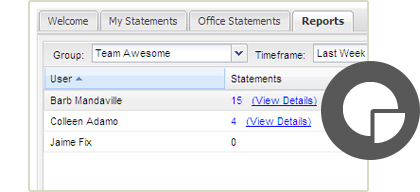
Report
n2record tracks all actions around a statement and provides real-time reporting capabilities such as:
- Number of statements taken
- Length of statements
- Claims representative compliance metrics
- Status of statements sent for transcription
These reports can be dynamically generated by claims representatives, office personnel or line of business managers. Being able to better understand your claims data provides real dollar gains around settlement, recovery, and customer service.
